If you’re reading this, then your daily personal and work life is probably dependent on information that is stored and accessed digitally. People and processes are working around the clock to keep these systems running smoothly. Likewise, others are working to disrupt, break into, or take control of these systems. The Ponemon Institute finds that 66% of small-medium enterprises experience a cyberattack within a year [1]. Cybersecurity aims to stop as many attacks as possible, but some attacks inevitably succeed.
Identifying a breach quickly is vital to minimize the damage – financial, operational, and reputational. But finding and then halting a cyberattack can be agonizingly slow – an average of 315 days [2], so there is lots of room for improvement. The average cost of a data breach could be as high as $5 million [3].
The Common Attack Pattern Enumerations and Classifications (CAPEC) initiative has defined more than 500 cyberattack patterns. Some examples of these patterns Abuse Existing Functionality, Collect and Analyze Information, and Inject Unexpected Items. Understanding these attack patterns is essential for analysts, developers, and IT architects to build effective cybersecurity systems.
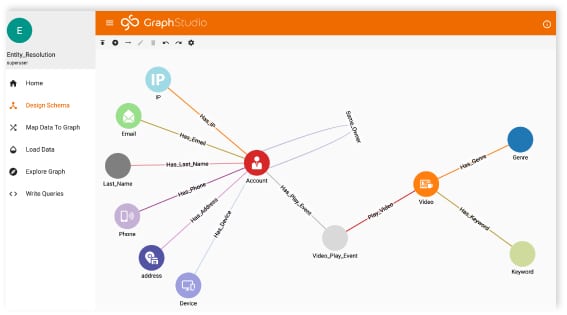
A graph data and analytics platform is an excellent way to model and search for these patterns, because graphs ARE connected data. To stop or detect cyberattacks, you need to be able to recognize the patterns, and trace them both upstream to their sources and downstream to your resources that are at risk. The patterns can be long, or wide with many things happening in parallel, or both long and wide. In this figure, we trace back from an alert to the login event and IP address that originally triggered the alert.
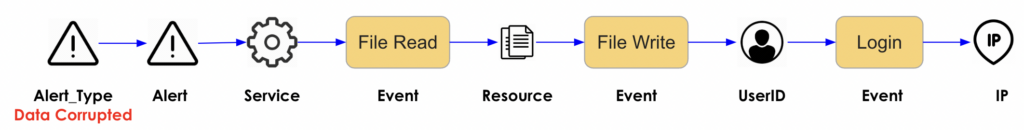
Figure 1. A linear path of activity
Often an attack is the work of relatively few perpetrators. This is the case with DDOS flooding attacks: a few IP addresses or user IDs are sending a very high number of requests to the targeted servers.
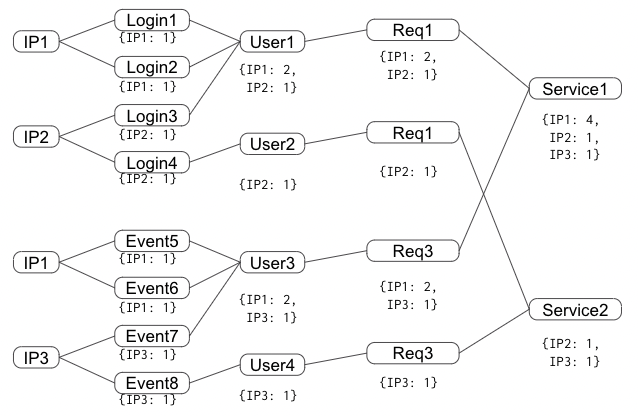
Figure 2. Tracing the IP addresses, events, and users that are making requests to particular servers
Graph platforms can integrate multiple data sources and process them in real-time: Information from many different microservices, user profiles, and user authorization systems all need to be looked at together to understand the activity, track down, and stop perpetrators.
Our book Graph-Powered Analytics and Machine Learning has an entire chapter on cybersecurity with graph analytics, with example queries running on TigerGraph Cloud.
Get your free copy of the book today to learn about graph analytics concepts and use cases.