by Parker Erickson and Victor Lee
Anti-Money Laundering (AML) refers to the set of laws, regulations, and procedures aimed at preventing and detecting money laundering – the concealment of illegally obtained funds, through the creative use of transactions. A common money laundering pattern called “layering” uses a mesh of mostly ordinary-looking transactions among colluding businesses and individuals that funnel money from one source to a target destination.
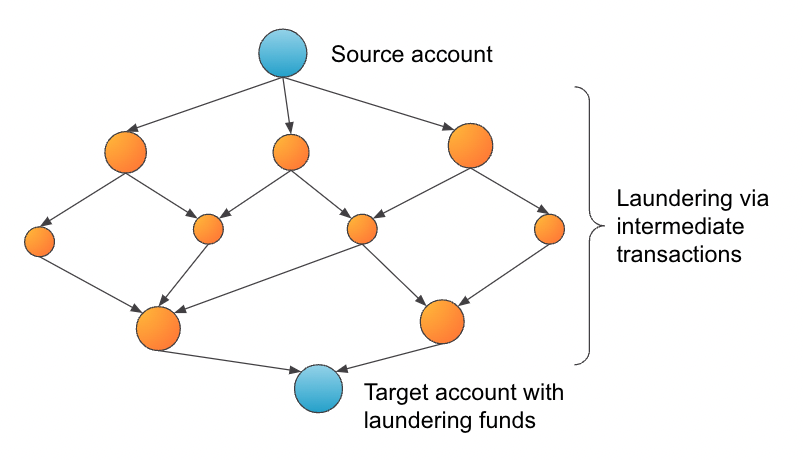
Money laundering through layering
To comply with government regulations, financial institutions build and operate systems that aim to flag potential money laundering behavior, typically done with hard-coded rules. However, due to the complexity of financial transactions and the various legitimate reasons for certain patterns of behavior, these systems often generate a significant number of false positive alerts. As the number of transactions grows worldwide, financial institutions are struggling to keep up with these alerts in a scalable manner, all while having to identify the changing patterns criminals undertake to prevent getting caught. To meet this challenge, more financial institutions are looking towards utilizing machine learning to help sift through the mountain of alerts in order to find suspicious activity.
The AML Investigation Process
The anti-money laundering process starts with the alerting process. In conventional AML systems, a set of alert rules are applied to transactions and the parties involved. A human investigator may need to take a look at flagged activity to judge if it is unusual for the party in question. If it is unusual, the party is elevated to a case status, where a further human review of the activity in question is used to determine if the activity is suspicious and should be reported to the appropriate government authorities. If that is the case, a Suspicious Activity Report (SAR) is filed, and the financial institution has completed their regulatory requirements. If a financial institution fails to report suspicious activity, they become open to being investigated and fined by the regulatory bodies.
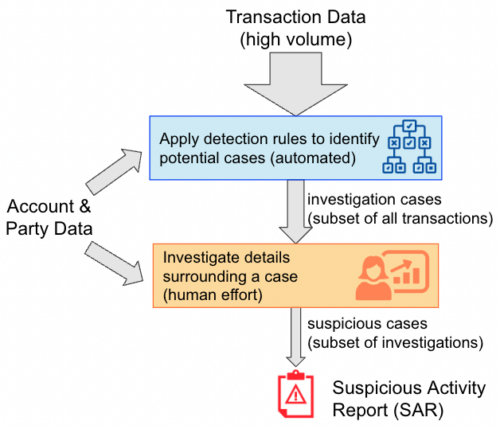
The AML investigation process
Financial institutions need to be as proficient and accurate as possible at detecting money laundering to satisfy regulators. The most efficient method is to improve the alert rules so that there are fewer false positives (alerts that turn out not to be real money laundering) and few false negatives (real money laundering that wasn’t detected). In practice, false positives are the bigger problem. Imperfect screening tends to flag too many transactions, and all those extra alerts (false positives) translate to higher human investigation costs.
Why Graph Machine Learning?
In order to reduce these false positive alerts while maintaining the rate in which suspicious activity is flagged, many institutions are turning towards machine learning (ML) to classify transactions and prioritize the alerts to be investigated. This is because machine learning is able to take a large number of data characteristics (or “features”) and then find the right balance of those factors that optimizes a goal, such as catching 98% of money laundering with a minimal amount of false positives. Conventional machine learning has proven to be helpful, but it is not enough.
Institutions are turning to graph machine learning to reduce their false positives and thereby lower their operating costs, by 10%, 20%, and more. Graph is able to provide this boost because it analyzes relationships. Money laundering only becomes apparent when the connections between parties and events are analyzed. Two types of connections are important:
- Connections between individuals (e.g., beneficial ownerships, politically exposed persons, etc.)
- Flows of money between accounts (e.g., cycles of transactions, mule accounts, etc.)
Graph machine learning is a subfield of machine learning that utilizes a graph data structure to either generate features for traditional ML models such as XGBoost, or native graph ML models such as Graph Neural Networks. The core idea is to incorporate information about the relationships between different entities in a complex system. The financial service space is a perfect space to apply these techniques, due to the core form of data – financial transactions – being inherently a relationship between different entities – accounts and parties. As AML is all about determining if relationships between accounts is suspicious activity, it makes it a natural fit to apply graph machine learning.
Graph Machine Learning Techniques
In the anti-money laundering space, there are a few different techniques for incorporating graph structure into ML pipelines. The first is to calculate graph features for existing ML models such as XGBoost, Random Forests, and more. These graph features can be standard graph algorithms, such as PageRank or Shortest Path, or they can be patterns that are tailored to the particular bank’s data model and customer behavior, such as “the number of previously flagged Parties within 3 degrees of separation from the Party in question, weighted by the size of the transactions.”. Another method is to use graph neural networks which natively incorporate relationships between entities in the machine learning model, without the need for explicit feature extraction.
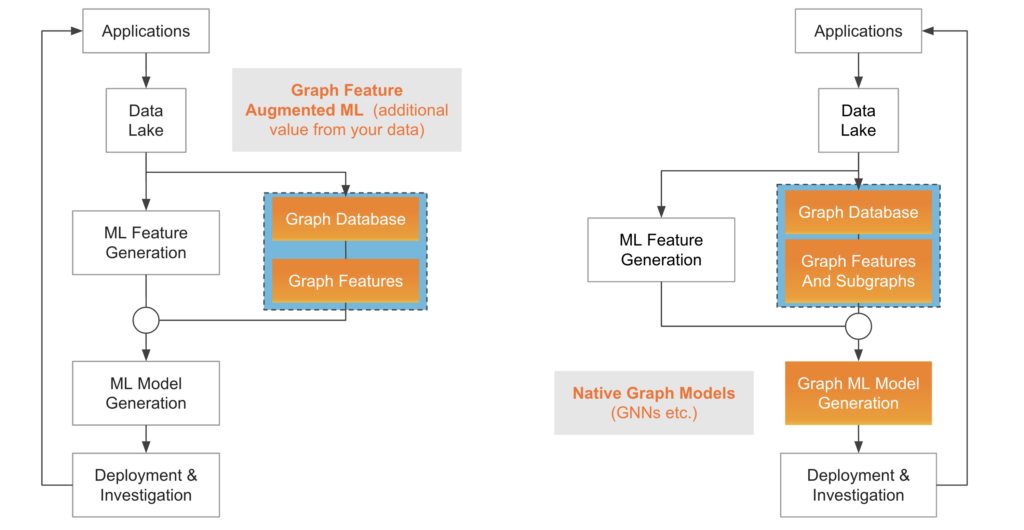
Two methods of Graph Machine Learning. Pictured on the left is incorporating graph features with traditional ML models, while the right represents utilizing native graph ML models such as GNNs.
TigerGraph is a leader in graph feature generation due to its scalability (10s of Terabytes of graph data), as well as execution speed due to its natively distributed and massively parallel processing (MPP) architecture. TigerGraph’s support for Python and several ML libraries make it simple for data scientists to add graph features or graph machine learning to their existing ML workflows.
Graph Features And Traditional Machine Learning
Various graph features can be used to help traditional machine learning models perform in anti-money laundering and financial crime detection in general. Here, we are going to give an overview of 3 main classes of graph algorithms that can be used for graph features:
- Shortest Path: Shortest path algorithms can answer questions like “how close is the party of interest to a party that has exhibited suspicious behavior in the past?”, which may provide a useful signal to the downstream machine learning model.
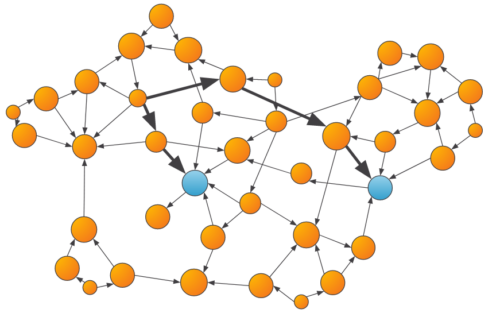
An example of shortest path algorithms determining how close a party is to a known suspicious party.
- Centrality: Centrality algorithms, such as PageRank, can measure the influence of a vertex on others within the graph, which can be a useful feature in the ML model, especially when used in conjunction with if the influential parties were known to be suspicious in the past.
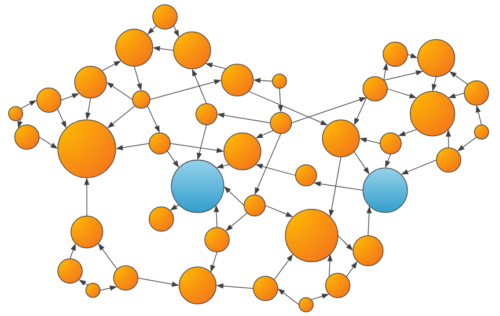
An example of the output of a centrality algorithm, where larger scores are denoted by larger vertices. Parties that are more central have more transaction inflow and outflow, which may be a suspicious behavior.
- Community Detection: Community algorithms, such as Weakly Connected Components (WCC) or Louvain, can be used to determine groups of vertices that share common characteristics or heavily interact with each other. Once the communities are determined, features such as the community size, the number/amount of transactions within the community, and more, can be calculated and passed to the ML model.
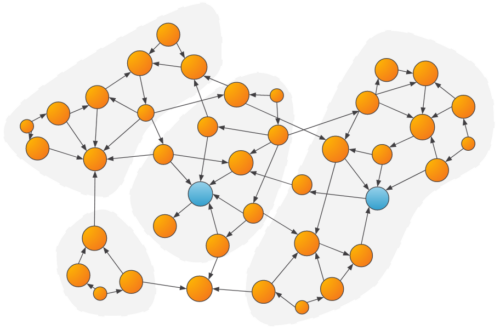
Example of communities detected within a graph. Parties that are within the same community as a suspicious party might be more likely to be suspicious as well.
Through these algorithms, we can then perform other manipulations or aggregations to the data. For example, how many parties within a community have had a SAR filed on them? How many unique addresses are within the community? What are the most influential parties within the community as measured by PageRank? All these different types of features usually result in top feature importance values when analyzed via SHAP or XGBoost feature importance measures.
Graph Neural Networks
Graph Neural Networks (GNNs) are a flavor of neural network architecture that operates on graph data structures. These algorithms take into account both the numerical attributes of vertices in the graph, but also the edges between the vertices explicitly. This method can result in an additional accuracy lift over just incorporating graph features into traditional machine learning models. Additionally, they can provide an extra layer of explainability to investigators, as the model not only provides feature importance, but also the importance of the edges between different vertices in the graph.
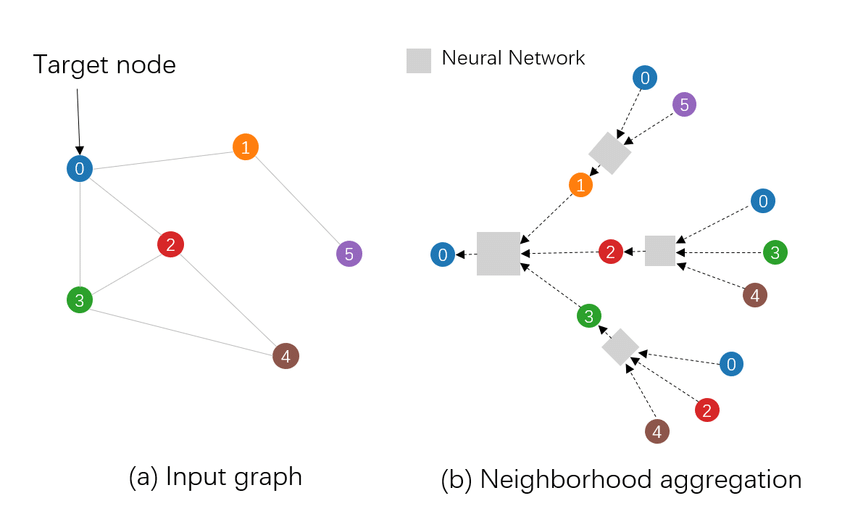
Example of how a Graph Neural Network makes its predictions.
Image Source: https://www.researchgate.net/figure/Given-an-input-graph-a-GNN-predicts-the-label-of-the-target-node-eg-the-blue-node_fig2_346143176
Conclusion
In the dynamic arena of Anti-Money Laundering (AML), the conventional rule-based approach to spotting potential financial crimes is yielding to the transformative potential of graph machine learning. The escalating volume of financial transactions and the prevalence of false positive alerts have catalyzed the adoption of innovative techniques that prioritize investigation efficiency. Graph machine learning, with its ability to decipher intricate relationships between entities in financial data, emerges as a pivotal solution. By leveraging graph features and advanced Graph Neural Networks, institutions can not only mitigate false positives but also enhance investigative accuracy. In this landscape, TigerGraph’s prowess shines – its scalability and performance in generating graph features have positioned it as a leader. As financial institutions navigate the complex terrain of AML, the convergence of graph machine learning and TigerGraph’s capabilities promises a more resilient defense against money laundering while optimizing resource allocation for investigations.
TigerGraph has demo examples of graph analytics for financial crime detection, which you can try for free on TigerGraph Cloud.
Download TigerGraph’s O’Reilly book Graph-Powered Analytics and Machine Learning. This book uses use case examples, including financial crime detection, to teach about graph analytics and graph machine learning.


